Living in a Cyberwar Glass House
Any football fan can tell you that offense makes the highlight reel, but defense wins championships.
The U.S. has been engaging in a global cyberwar for roughly a decade now, attacking Iran's nuclear program and North Korea's missile program.
But what do our cyber defenses look like? You might be shocked.
“About 75 percent of the devices that are control systems are on Windows XP or other nonsupported operating systems,” said Daryl Haegley, program manager for the Office of the Assistant Secretary of Defense for Energy, Installations and Environment.
Haegley, speaking Thursday at an event hosted by OSIsoft, said the assessment was based on visits to 15 military sites. Microsoft stopped providing support for Windows XP in 2014. Haegley, however, said some of the systems that run DOD facilities are far older.
“A lot of these systems are still Windows 95 or 98, and that’s OK—if they’re not connected to the internet,” Haegley added.
Uh, no. It's not OK. It's not OK at all.
We are breaking things and picking fights with the world, but lack a clue for how to defend ourselves from a counterpunch.
Currently, the US offensive capability in cyber is one of the best in the world, but our defenses are sorely lacking due to a misunderstanding of what true cybersecurity is. We have been building cyber weapons but have essentially ignored cyber defense outside of the military.
Let me give you an idea of the immense scale of the problem we face.
The latest surveys show that small businesses need all the help they can get. In the last 12 months, hackers have breached half of all small businesses in the United States, according to the 2016 State of SMB Cybersecurity Report.
Half of all small businesses.
That's 14 million small businesses that got attacked last year.
1 in 3 small businesses don't things like firewalls, antivirus software, spam filters or data-encryption tools.
Ransomware attacks, which can cripple a small business, increased 50% over last year.
Of actual hacks themselves, 73% are financially motivated.
So what does that mean to you?
It means your W-2 is selling online for less than $8.
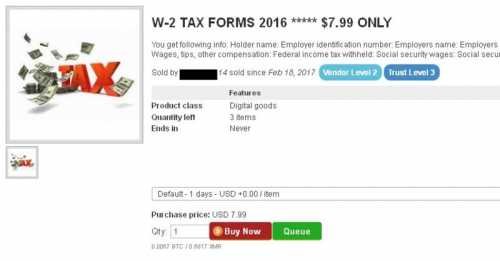
One vendor noted on his sale of W-2s that it “comes with 2015 data to fully complete the return.” The IRS requires the prior year’s adjusted gross income (AGI) on a return, so that costs a would-be scammer extra. One vendor IBM found was selling W-2 and 1040 returns as a package for $30 worth of bitcoin; if someone wanted AGI information, that was $20 more. Another cybercriminal had a bulk offer that promised data that was “fresh” for the 2016 season, and included W-2 data, date of birth, and the AGI figure. That was $50 in bitcoin per record.
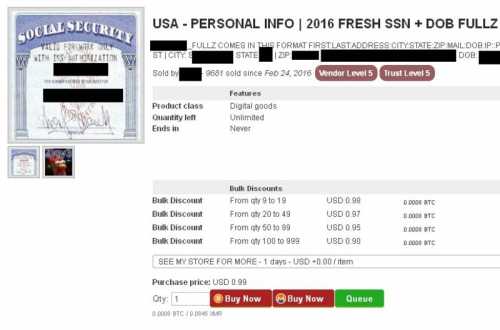
An individual’s tax data is far more valuable than their credit card data. Stolen credit card data might sell for $1 or be given away to establish credibility on the Dark Web, said Limor Kessem, executive security adviser of IBM Security.
I bet you thought your credit card info was worth more than a buck.
The volume of stolen information online is so enormous -$450 Billion on 2 billion records - that it's pushing the price down to dirt-cheap.
We are losing the war against criminal hackers who just want our money. Even squirrels are beating us.
What will happen if full-time, paid professionals of nation states want to do us harm?
I doubt we want to know the answer.

Comments
Can we use this info to fight back and win against the 1%?
Either use this info to scare the 99% into fully distrusting the system and thus changing it for the better, or, get a bunch of anti 1% er hackers together to totally destroy the current economy and make it become the Monopoly money that it truly is.
American companies outsourcing their databases to scammers
India and SE Asia have have a huge industry of what I name as "call center scammers". These are the groups that call up people in English speaking countries and pretend to be from the IRS (or Canadian IRS, etc) and demand missed tax payments or they will be jailed immediately. Or the scams of pretending to be Microsoft support and claiming your license ran out. These various types of scams depend on getting databases to profile people and then aggressively go after their targets.
I got interested in this scam call centers after I got a couple of calls from the IRS scammers, and when a college buddy told me his sister-in-law got taken for $8,000. I listened to the recording and a bit too bizarrely so never answered, and anyway, come and get me coppers.
Several months ago a big scam center was busted which employed several hundred people and occupied a number of floors of a building. One of the guys arrested said the owner spent a lot of his money buying various databases.
And then a buddy told me that he called a legit call center in India on a modem issue. He noticed that every time he called, soon afterwards Indian scammers would start calling. To me it was obvious that somebody was taking the internal databases and selling them, or even using it themselves.
so when US companies outsource their support, they pretty much are handing over their customer database to scammers and data thieves--and I believe they know it. But the real moral of the story is that the US has problems with data theft for the simple reason of greed and cost reduction--it is not a matter of some super genius hacker outsmarting the system most often. US companies are literally selling off the jobs and assets of the American people to make profits easier to make.
gj, you have missed the train (not the one blocked by a swan)
Hillary has been right all along about our cybersecurity being victim to Russian hacking, or should I say gnawing.
Please consult Wikileaks on squirrels:
Russia is the largest Eurasian country. There is no doubt that malicious cyber attacks you describe are the nefarious doings of Russian squirrels, secretly brought in, disguised as fur hats. Please apologize to the Bots, or we shall have to send some American squirrels after you.